Centium provides expert vulnerability assessments, scanning, and penetration testing services to help organisations uncover, understand and remediate security weaknesses across networks, applications, and cloud environments.
With cyber threats constantly evolving, identifying security weaknesses before they are exploited is critical. Vulnerability assessments and scanning provide a proactive approach to identifying known vulnerabilities in your systems and infrastructure. When combined with penetration testing and technical assurance, these services help build a resilient cybersecurity posture.
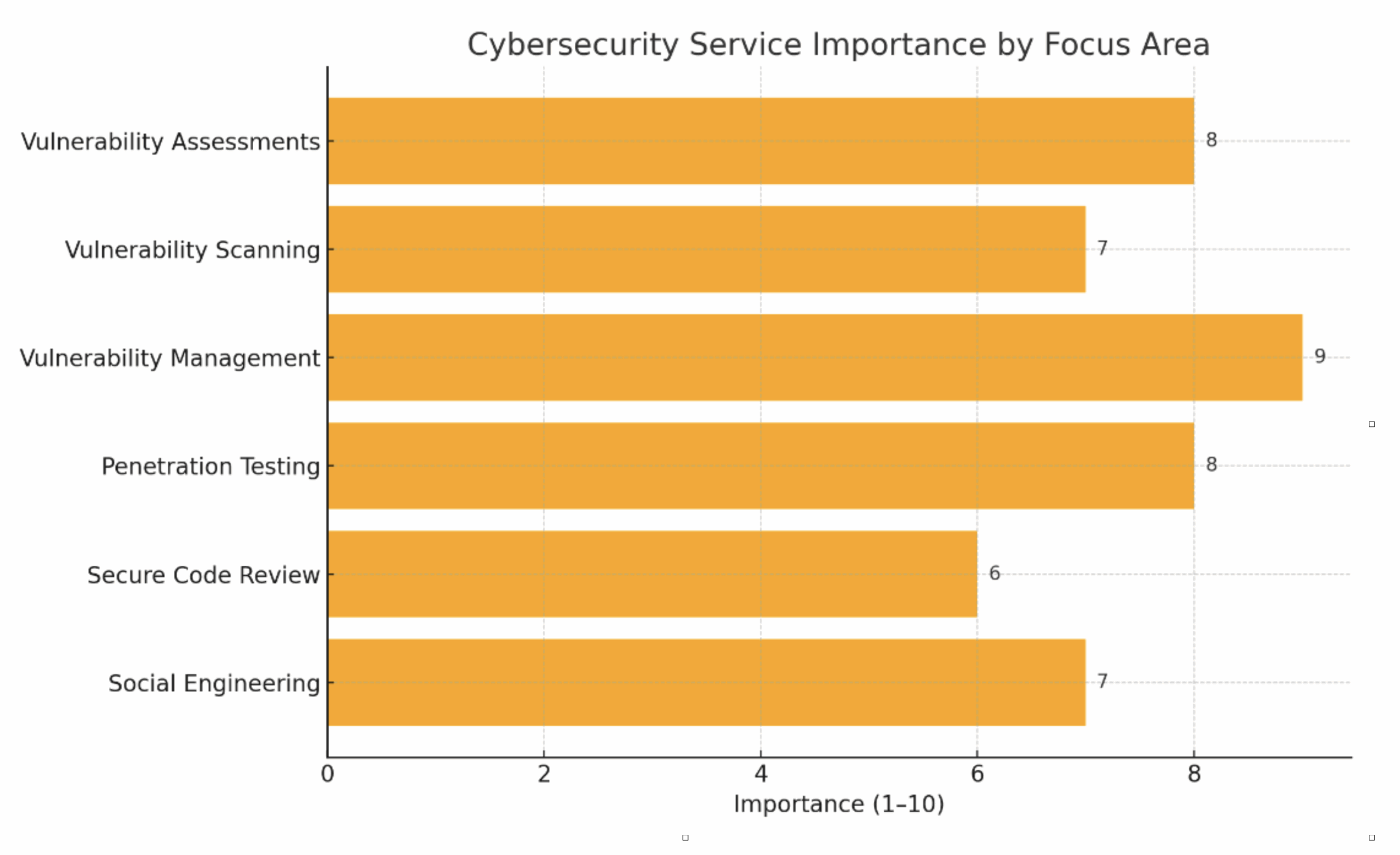
Centium conducts comprehensive vulnerability scans across internal and external networks, systems, and cloud assets. Our assessments combine automated scanning tools with manual validation to eliminate false positives and ensure accurate results.
Our penetration testing services simulate real-world attacks to identify potential exploits across:
We also provide cloud penetration testing for platforms like Microsoft Azure and AWS.
Beyond technical vulnerabilities, we can also test your organisation’s human and physical security controls to give you a more holistic view of your security posture. This includes:
Our team reviews application source code to identify vulnerabilities early in the development lifecycle—reducing risk before deployment.
Centium’s cybersecurity services are grounded in independence, technical rigour, and real-world expertise. Our team has decades of experience supporting organisations, critical infrastructure, and regulated industries. We provide clear, actionable insights without the noise.
All assessments include a detailed, prioritised report with:
Where required, we can support your team post-assessment with additional advisory support.
Safeguard your systems with expert vulnerability assessments and technical assurance from Centium. Contact us today to discuss your needs or schedule a consultation with our cybersecurity team.