A cyber security penetration test (colloquially known as a pen test and sometimes described as ethical hacking) is an authorised simulated cyberattack on a computer system, performed to evaluate the security of the target system.
Pen tests are frequently mentioned in the media, yet when they are reported, their results are never released. That keeps the results confidential and secure – and ensure hackers can’t decompile them for their own further nefarious uses. However, for the external viewer, there is always an element of mystery and IT technical complexity surrounding these tests.
At the end of the test/s, a report is delivered to the client showing the weaknesses that have been found, so that the client can implement measures to reduce them. And there are other real benefits to pen testing, which we outline further below.
Potential benefits of a pen test include:
Some of the potential drawbacks are:
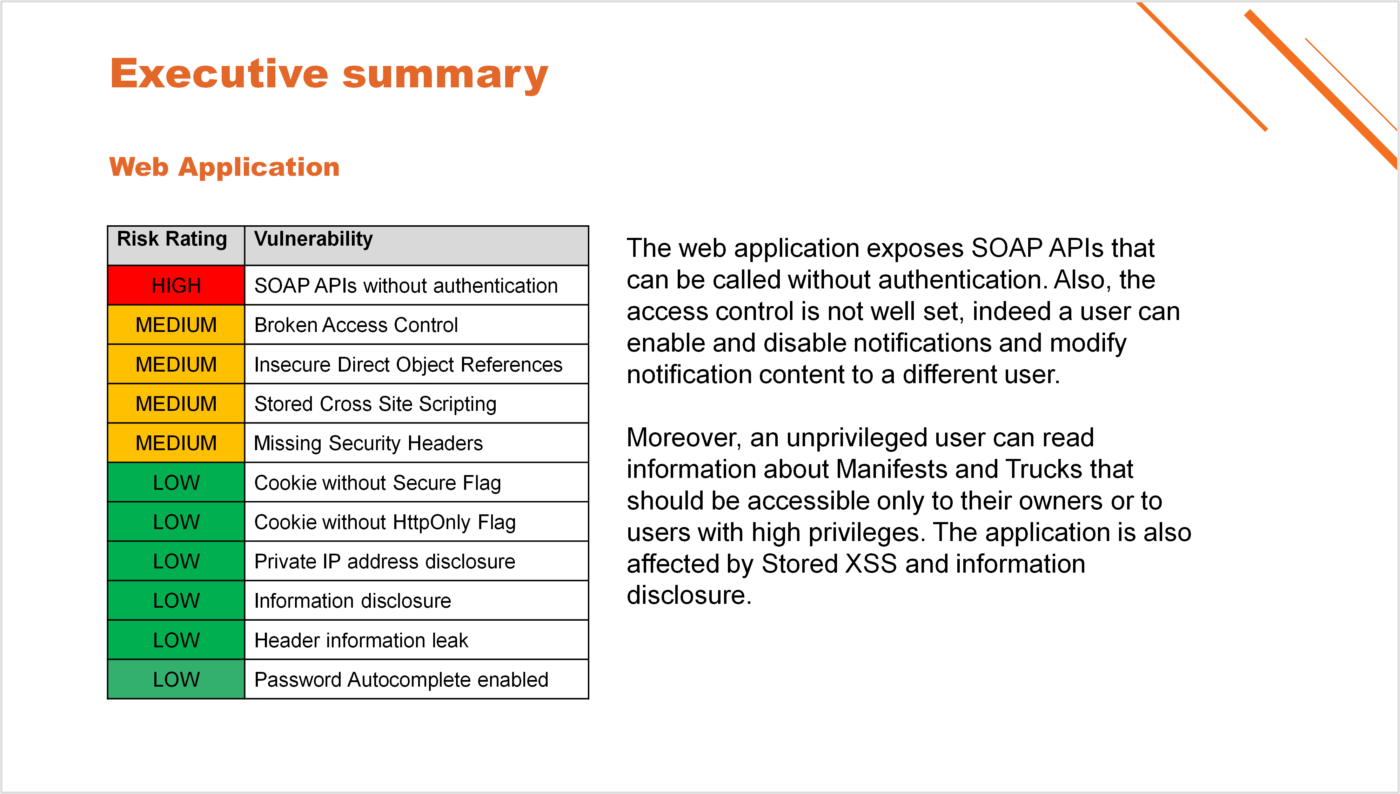
So, with all that mystery and IT technical complexity surrounding it, what does a pen test report look like? It will all depend on the outcomes and findings of those tests, and vary as much as the tests themselves. Always technical in nature and usually very confidential, the Executive Summary of a straight-forward pen test report can look similar to the example below.

There are numerous benefits from employing penetration testing, which clearly outweigh the potential drawbacks:
Protect corporate reputation and company profile Pen testing helps an organisation avoid data incidents that may put the company’s reputation and reliability at risk.
Identify and assess security threats Organisations can more efficiently anticipate potential security threats and avoid illegal or unauthorised access to crucial information and critical systems through executing regular and complete pen testing.
Avoid application and network downtime Pen testing helps an organisation escape financial losses by proactively detecting and addressing threats before security breaches or attacks take place.
Service outages and cyber events are expensive Regular pen testing reduces the risk of incurring these expenses by the organisation than to face exceptional losses, commercial confidentiality, service availability and customer disruption.
Compliance obligations The reports produced by the pen tests can assist organisations in demonstrating compliance with Government or regulatory body standards, such as PCI or ISO 27001 certification. It assists the organisations to demonstrate ongoing due diligence to auditors by maintaining required security controls.
Some companies make the mistake of starting a pen test too early on a network or system deployment. When a system or network is being deployed, changes are constantly occurring, and if a pen test is undertaken too early in that process, it might not be able to catch possible future security holes. In general, a pen test should be done right before a system is put into production, once the system is no longer in a state of constant change.
A pen test is not a one-time task. Networks and computer systems are dynamic — they do not stay the same for very long. As time goes on, new software is deployed and changes are made, and they need to be tested or retested.
How often a company should engage in pen testing depends on several factors, including:
Centium has partnered with two specialist Pen Testing firms who carry out the vulnerability assessments and penetration tests required to detail all risks pertaining to systems and applications in an organisation.
When combined with Centium’s in-house expertise in cyber and IT risk management services, we are able to provide our clients with a comprehensive vulnerability assessment service. This service is further enhanced by a tailored knowledge sharing and training program, which in turn enhances the effectiveness and timeliness of any identified corrective actions.
With Centium as your cyber security partner, you can rest assured that your valuable information and IT systems are protected, and you will be much better placed to mitigate potential cyber-attacks.
Centium specialises in cyber security and information management. Discover how we can help today by contacting us for a free consultation.